What is the Role of JAF Consulting in REDCap Validation?
“Reducing risk while strengthening research electronic data capture (REDCap) processes for institutional organizations and teams.”
The fundamental goal of JAF Consulting Inc. is to provide a risk-based approach to the validation of REDCap’s Electronic Informed Consent (eIC) module, Electronic Data Capture (EDC), eDocs (21 CFR Part 11 file upload feature), all other REDCap core functionalities to ensure compliance with current FDA regulations and guidelines per Good Clinical Practices.
Validation Approach:
The JAF risk-based validation approach provides a very cost effective solution for the implementation of eIC, EDC, and eDocs (file upload) for the REDCap system. Risk-based validation includes as-built configuration verification along with validation testing of user / functional / configuration requirement specifications. The current installation of REDCap v 10or higher has the eIC, EDC, and eDocs (file upload) included as part of the installation file. Industry accepted Software Development Life Cycle (e.g., Agile, Waterfall, Rapid Application Development, Lean, Iterative, Spiral) model is adopted to implement the REDCap system at each client site. Based on the software development lifecycle model, risk assessment is performed on project and functional levels. Having direct impact on patient safety this system falls in the GxP major category. Functional risk assessment is performed on critical business requirements, 21 CFR part 11 requirement(s), data integrity requirements infrastructure, security and non-functional requirements. Based upon the outcome of the assessment, all identified risks are mitigated through validation testing.
JAF deliverables provided for the validation effort include:
What makes JAF a perfect partner for your REDCap implementation and validation?
JAF has implemented the REDCap application at various client sites utilizing numerous use cases. The JAF team has been involved with :
Possible Risks and Threats of not validating REDCap found by JAF:
A non-validated product can result in not meeting the expectations of regulatory agencies.Following are examples of frequently observed compliance gaps:
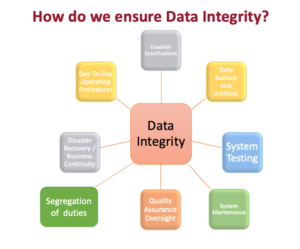
How does JAF ensure system integrity:
We meet the ALCOA+ guidelines, through